It’s Tuesday and you know what that means, Guest Post Tuesday!!
Get excited for my favorite part of the week where I get to showcase the work of fellow Substack authors to my amazing community.
and I have been in contact for a bit trying to set this up. His Substack is quickly becoming a must-read for anyone curious about using AI to actually build things.What makes Doug’s work stand out is his no-fluff, experiment-driven approach. He doesn’t just talk about what AI could do—he shows you what it can do right now, with real tools, real builds, and real takeaways. Whether you're technical or just AI-curious, his work makes complex ideas feel accessible and actionable.
This aligns with my goals so well (just on a different topic) that I had to have him write something up for me. So here is an excellent breakdown of Vibe coding security.
Enjoy!
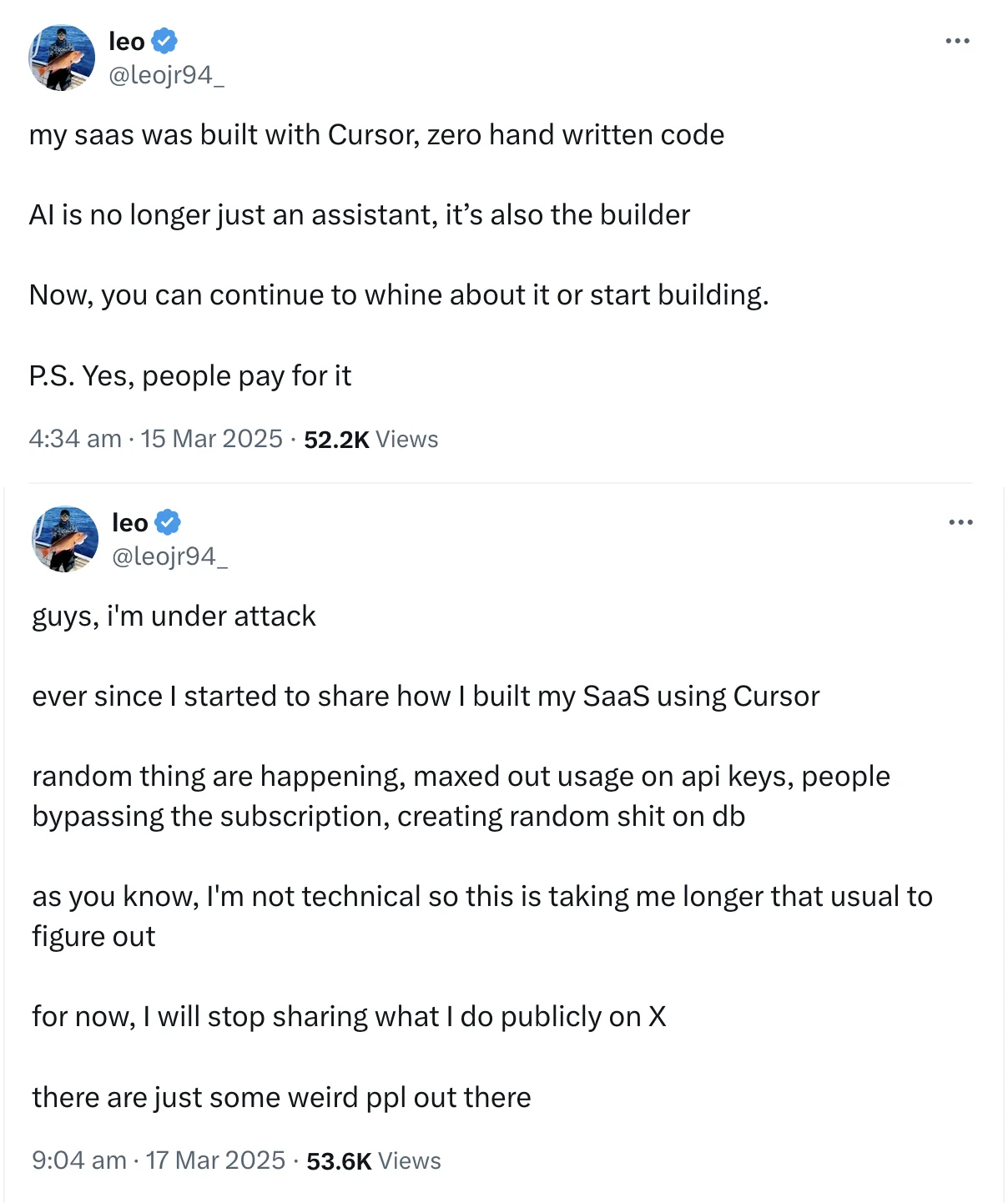
Vibe coding is your superpower.
But every superhero has a weakness. For many vibe-first founders, that weakness is security. You're moving fast, but are you leaving gaping holes in your foundation? Let's talk about the security risks you can't afford to ignore.
Don't let this be your story.
Security isn’t something that comes bundled out of the box when you’re vibe coding, and that can lead to some pretty serious consequences for you and your product.
So what should you do? Go through these basics to make sure you’re leaving yourself exposed.
Authentication
Use a trusted authentication provider: Rolling your own auth is like performing surgery on yourself. Stick to battle-tested providers like Auth0, Firebase, or Supabase. They've already solved the complex security challenges that would take you months to figure out.
Enable Multi-Factor Authentication (MFA): This is your digital bodyguard. By adding an extra layer of verification beyond passwords, you're making it exponentially harder for bad actors to breach your system. Most users are now expecting this level of security. Most auth providers offer this.
Handle password resets and session management like a pro: Implement secure password reset flows that expire tokens quickly and prevent replay attacks. Manage user sessions intelligently, with the ability to log out from all devices and track active sessions.
Authenticate EVERY single API request: Never trust the client-side. Every request to a protected endpoint must go through a robust authentication check. No exceptions.
Pro tip: Never, ever think you can build secure auth from scratch: Authentication is a deep, complex rabbit hole. The most experienced security experts spend years at this and their job is never done. Save your energy for your core product.
Middleware Protection
Add middleware to shield sensitive routes: Think of middleware as bouncers for your digital club. They check credentials, verify permissions, and block unauthorized access before a request even reaches your main application.
Role-based access control (admin, user, guest): Create a clear hierarchy of permissions. Each role should have defined capabilities, this minimizes the potential blast radius of a potential security breach.
Validate user identity and permissions before processing requests: Don't just check if a user is logged in. Confirm they have the right to perform specific actions. An admin shouldn't have the same access as a regular user.
Sensitive Data Handling
Store secrets in .env files: Environment variables are your secret vault. Keep API keys, database credentials, and other sensitive information out of your codebase.
NEVER expose secrets to client-side code: Client-side code is like a postcard—anyone can read it. Keep your sensitive information strictly server-side.
Always add sensitive files to .gitignore: Prevent accidental commits of .env files or other sensitive configurations. One slip-up can expose your entire infrastructure.
API Security
Rate-limit your API endpoints: Protect against brute-force attacks and potential DDoS scenarios. Implement intelligent rate limiting that balances security with user experience.
Ensure front-end communicates through API endpoints, not directly to the database: Your database should be a fortress. Always route data access through carefully designed and secured API layers.
Error Handling
Display generic, user-friendly error messages: Users don't need (or want) to know the intricate details of what went wrong. Keep error messages clear but non-technical.
Log detailed errors server-side only: Comprehensive error logging helps you debug, but those details should never reach the end-user.
Never reveal sensitive information in logs: No stack traces, no database details, no hints that could help a potential attacker understand your system.
Input Validation
Sanitize ALL user inputs: Treat every piece of user input like it's trying to hack your system—because it might be. Strip out potentially malicious scripts and unexpected characters.
Prevent SQL injections and cross-site scripting (XSS): These are classic attack vectors. Before your app does anything with user-provided information, make sure it's safe and in the format you expect. This simple step blocks many common security threats.
Validate everything server-side: Client-side validation is for user experience. Real security happens on the server.
Bonus: Use DOMPurify for extra protection: This library is a champion at cleaning up potentially dangerous HTML and preventing XSS attacks.
Database Security
Choose a trusted platform (I like Supabase): Modern database platforms come with built-in security features that would take months to implement manually.
Set up row-level security: Ensure users can only access the data they're supposed to see, right at the database level.
Use ORMs over raw queries: Object-Relational Mappers provide an additional layer of protection and abstraction.
Avoid SQLite in production: It's great for development, but production environments need more robust, scalable solutions.
Code Cleanup
Run
npm auditafter your MVP: Regularly check your dependencies for known vulnerabilities.Remove unused packages: Every extra package is a potential security risk. Keep it lean.
Set up GitHub Dependabot: Automate your dependency updates and security patches.
Employ a "linter" – a tool that analyzes your code for potential errors and style issues: These warnings aren't just about code aesthetics; they frequently indicate underlying problems that could be exploited for security vulnerabilities. Make sure to address every single one.
Remove those sneaky
console.logmessages used for debugging: They're not just clutter; they can accidentally leak sensitive information.
Monitoring
Watch your logs: Modern monitoring tools give you real-time insights into your application's health and potential security issues. Use tools like Supabase logs, Vercel analytics.
Track failed logins and request spikes: Unusual patterns can be early warning signs of an attack.
Stay vigilant: Monitoring isn't a set-it-and-forget-it task. Regularly review your logs and metrics.
Hosting
Choose secure, well established platforms (Vercel, AWS, GCP): These providers invest millions in security infrastructure you can't replicate alone.
Enable firewalls and DDoS protection: Create multiple layers of defence against potential attacks.
Keep auto-updates on: Security is an arms race, and staying current is your best defence.
This list isn’t exhaustive, but should make sure you’ve got a solid base to build a dependable vibe-coded solution.
It’s also not about killing your creative momentum. It's the foundation that lets your product scale, grow, and truly succeed.
For more direct strategies on building fast tech powered by AI subscribe to Build Fast AI. Let's go!
We want to hear from you!
What was something you surprising you learned today?
When was the last time you checked your password settings—or are you trusting default everything?
What’s one thing on this list that confused you?
If you know someone who is a developer or just building apps as a hobby, be sure to share this with them by restacking this post.
Want to be featured next?
Want to get visibility from a new audience?
Brave enough to share your work?
If you are interested in participating in a future Guest Post Tuesday like Doug, send me a direct message with your topic idea. If it’s something I think will resonate with the rest of the community I’d love to set something up.
Huge thanks again to
for participating today with this insightful post.Until next time…







Great post - vibe coding seems to be what's "in" right now, so great to share these parameters!